10 Cybersecurity Tips to Protect Your Data from Ransomware Attacks
Ransomware is a malicious trend where encryption is used to hold people’s data for ransom. Unfortunately, it has become a popular way to extort money from unsuspecting businesses. This is done through promises of restoring the encrypted data.
Of course, there is no guarantee that this promise will ever be delivered on. Typically, file servers, database services, virtual machines, and cloud environments are hit.
There are a few different ways that ransomware can gain access to a computer. Generally, it exploits a security hole or tricks someone into installing it. One of the most common ways is via phishing spam – using emails with attachments that look like they can be trusted.
Once they’re downloaded and opened, they can take over the computer. Attacks that exploit security holes don’t even require a user to accidentally let them in.
Businesses need to adapt as digital trends and threats change. There are constantly new things to respond to in the digital world. They can lead to new avenues for growth, but also the potential for issues. Malicious software such as ransomware can be a scary prospect for anyone. A digital transformation might be needed to ensure you’re as protected as possible.
Thankfully, there are ways to improve practices and software to fight against ransomware. Here are some steps you can take to ensure your data is as protected as possible.
Tips to Protect Your Data from Ransomware Attacks
#1 Use a trusted firewall and antivirus.
No antivirus is perfect, but it can go a long way to preventing attacks. Some antivirus software even has added ransomware protection. You’ll want to use one that comes with email filters that can block known phishing emails. They can also have a malicious network filter that can help to keep you safer online. Make sure your system is protected and your software is up to date, and that scans are run regularly. There is lots of fake software around, so it’s important to use an antivirus from a reputable company.
#2 Keep all operating systems up to date.
Many past attacks were so serious because people were not updating their systems. One case showed hundreds of thousands of computers in 150+ countries to be outdated.
Updates ensure that you benefit from the latest security patches. Attackers are always looking to exploit vulnerabilities in unpatched applications and operating systems. Therefore, keeping your operating system patched and up-to-date is essential. You will have fewer vulnerabilities to exploit, lowering your chances of being targeted.
#3 Make sure staff always think before clicking on anything.
No matter how good your software, you need to have switched-on employees to protect your business. Social engineering is currently the main vector for ransomware. This refers to manipulating or deceiving someone to gain control over computer systems.
The hacker might use the phone, email, or direct contact to gain illegal access. Training employees on how to recognize and defend against cyberattacks, though, is often overlooked. Yet it could possibly be the most important key in combating ransomware attacks.

Ensure you have appropriately trained your staff in identifying suspicious calls and emails. Keep their training up to date so they know what to look out for. Phishing simulation programs can be used to maximize the effectiveness of training.
There are also some easy and effective tricks that can help. For example, get staff to hover first over any links in an email, not click on them immediately. They can then check that the destination URL matches the destination site expected. Attackers will often claim they’re from the IT department. They then trick staff into downloading malware or exposing data. Make sure staff know to contact their IT department if they receive suspicious calls or emails.
#4 Encourage employees to discuss cybersecurity openly.
Collaboration is the best way to get most things done. When your employees are working together, everything runs more smoothly. This can also help with warding off these sorts of attacks. Sharing information and discussing suspicious emails or calls will ensure everyone is prepared. It helps employees to understand risks and be comfortable getting a second opinion. Fostering collaboration could make staff less likely to install suspicious files without checking.
The personal details of 9 million customers were accessed after EasyJet faced a cyber attack in May 2020, with 2,200 customer credit card details stolen by the hackers.
#5 Encrypt everything you can.
Encrypting as many things as possible will help to add another layer of protection. This will make you far less vulnerable to opportunistic attacks.
Using a VPN can help hide your real IP and location from hackers by encrypting your traffic. You will especially want to use a VPN if your employees are accessing public Wi-Fi. It would be worth implementing a VPN for any mobile or remote employees.
#6 Scan all incoming mail.
Use content scanning and filtering on your mail servers. Google reports blocking more than 100 million phishing emails on their servers daily. In fact, 91% of cyberattacks begin with a spear-phishing email. Inbound emails should be scanned by software for known threats.
Any attachment types that could pose a threat should be blocked immediately. There are also browser plug-ins that inhibit the automatic download of malicious content. As already mentioned, employees should receive training in identifying anything that looks dodgy. There are some specific tips that they can use to manually scan emails themselves.
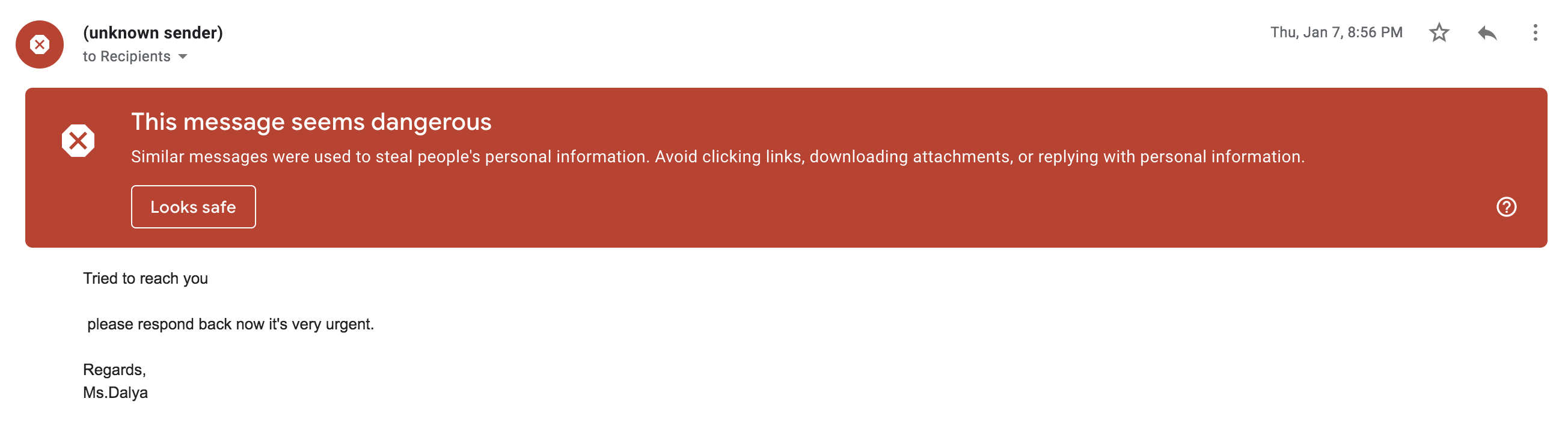
Train staff to check if incoming addresses match the name of the sender. Then, to see whether the domain of the company is correct. Make sure your email client displays the sender’s email address and not just their display name.
#7 Protect your phone lines.
Previous attacks have shown that they can also be initiated over the phone, not just via email. Ensure you have a reliable virtual office phone service. Unfortunately, VoIP attacks are on the rise, leaving phone systems vulnerable. You will want to ensure you have VoIP call recording.
This will help to identify problems and support your employees. Use an automated phone system to manage call volume, including potentially dangerous calls. Caller identification systems can authenticate calling numbers via certificates. Malicious sources of calls can also be tagged and blocked. Be sure to research the best call center software to ensure your contact center is supported.
#8 Protect files when sharing them.
Protect your information and privacy when sharing documents with people outside your organization. Password protect your documents so only select viewers will have access to them. Ensuring you have secure content will close up one potential hole for an attack.
#9 Regularly check the health of your websites.
Malware can impact website loading time, slowing it down as it mines for data. Hackers don’t always announce their intrusion immediately, while they gather information. Hackers may have directed files from another server to load along with your page. It is possible for undercover malicious activity to use your own server resources.
If your website is loading slowly, this could be the reason for it. You will need to intervene, protecting your files before the attackers hit.
#10 Regularly backup your data.
Even the best digital transformation and most secure systems can’t guarantee total protection. It’s unfortunate but true. You can lower your risks significantly, but there is always a chance that you could still be targeted. In most cases, once the ransomware has been released into your device there is little you can do. That is unless you have a backup or security software in place. With the right backup strategy, your files can survive an infection. In the unfortunate case that you do fall prey to an attack, you will need to make sure you’re in control of the situation. Perform backups of your data regularly and often. Ensure you have a good, trusted backup of all your information that you can restore any impacted files from.
It’s not recommended to give in to the demands of ransomware. Restoration of your files from a backup is the best way to regain access to your data. There are also options to recover lost data and files without giving in to the ransom demands. There are some initiatives that can help in a ransomware situation. But don’t rely only on their efficacy, make sure you and your business are prepared and protected.
Conclusion
Protecting your data will help safeguard your employees and information against an attack. However, it’s also important to do so for your customer service experience. Customers want to feel safe with the companies they engage with.
They want to be confident that their information is safe, too. So make sure you follow these steps to ensure safety for your business. But also to protect your customers and your overall reputation within your industry.








